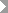SameSite Cookie Configuration for Live Data Connections
Configure your SAP on-premise data sources to issue cookies with SameSite=None; Secure attributes.
- Summary
- SAP HANA On-Premise
- SAP HANA on SAP Business Technology Platform (BTP) Cloud Foundry
- SAP S/4HANA, SAP BW or BW/4HANA, and SAP BPC Embedded with CORS Enabled by HTTP Allowlists
- SAP S/4HANA, SAP BW or BW/4HANA, and SAP BPC Embedded with CORS Enabled by ICM Rewrite Script
- SAP BusinessObjects BI Universe
Summary
A direct live connection (using CORS) from SAP Analytics Cloud to your SAP on-premise data source is a cross-site scenario. Your SAP on-premise data source, such as SAP HANA, SAP S/4HANA, SAP BW, and SAP BW/4HANA, issues cookies for authentication and session management. Every cookie has a domain associated with it. These cookies are considered by your browser to be third-party, or cross-site, meaning the domain of the cookie doesn't match the SAP Analytics Cloud domain in the user's address bar (ex: sapanalytics.cloud).
As of Google Chrome version 80, Chrome restricts cookies to first-party access by default and requires you to explicitly mark cookies for access in third-party, or cross-site, contexts. Chrome does this by treating cookies that have no declared SameSite value as SameSite=Lax cookies. Only cookies with the SameSite=None; Secure attributes will be available for cross-site access, and require secure HTTPS connections. Other browser vendors are looking at similar support for this new cookie behavior.
Action
You must configure your SAP on-premise data source to issue cookies with the following attributes:
- SameSite=None
- Secure
This will ensure Chrome and other browsers allow cross-site access to your SAP on-premise data source cookies from SAP Analytics Cloud. Without these settings, user authentication to your live data connections will fail, and Story visualizations based on these connections will not render.
Follow the steps in the sections below for your specific SAP system.
SAP HANA On-Premise
SAP HANA comes with a built-in Web Dispatcher, where an Internet Communication Manager (ICM) rewrite rule can be executed. To create and execute the rewrite rule, follow these steps:
- Log on to the SAP HANA system's operating system with the <SID>adm user.
- Go to /hana/shared/<SID>/profile, where
<SID> is your three-character system ID, and
create a rewrite.txt file with a text editor. Insert the
following script into the file, and save
it:
SetHeader sap-ua-protocol "" if %{HEADER:clientprotocol} stricmp http [OR] if %{HEADER:x-forwarded-for-proto} stricmp http [OR] if %{HEADER:forwarded} regimatch proto=http begin SetHeader sap-ua-protocol "http" end if %{HEADER:clientprotocol} stricmp https [OR] if %{HEADER:x-forwarded-for-proto} stricmp https [OR] if %{HEADER:forwarded} regimatch proto=https begin SetHeader sap-ua-protocol "https" end if %{HEADER:sap-ua-protocol} strcmp "" [AND] if %{SERVER_PROTOCOL} stricmp https begin SetHeader sap-ua-protocol "https" end if %{RESPONSE_HEADER:set-cookie} !strcmp "" [AND] if %{HEADER:sap-ua-protocol} stricmp https [AND] if %{HEADER:user-agent} regmatch "^Mozilla" [AND] if %{HEADER:user-agent} !regmatch "(Chrome|Chromium)/[1-6]?[0-9]\." [AND] if %{HEADER:user-agent} !regmatch "(UCBrowser)/([0-9]|10|11|12)\." [AND] if %{HEADER:user-agent} !regmatch "\(iP.+; CPU .*OS 12_.*\) AppleWebKit\/" [AND] if %{HEADER:user-agent} !regmatch "\(Macintosh;.*Mac OS X 10_14.*(Version\/.* Safari.*|AppleWebKit\/[0-9\.]+.*\(KHTML, like Gecko\))$" begin RegIRewriteResponseHeader set-cookie "^([^=]+)(=.*)" "$1$2; SameSite=None; Secure" RegIRewriteResponseHeader set-cookie "^([^=]+)(=.*; *SameSite=[a-zA-Z]+.*); SameSite=None; Secure" $1$2 RegIRewriteResponseHeader set-cookie "^([^=]+)(=.*; *Secure.*); Secure" $1$2 end - Start SAP HANA Studio.
- Select the HANA System connection.NoteIf the SAP HANA system is multi-tenanted, use the System database connection.
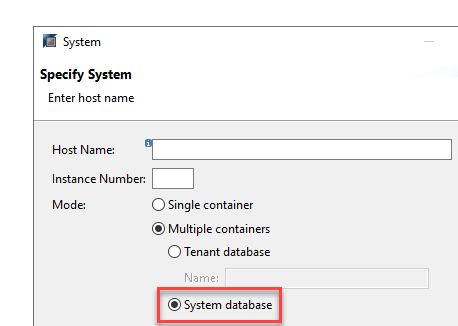
- Right-click the HANA system. On the context menu, select .
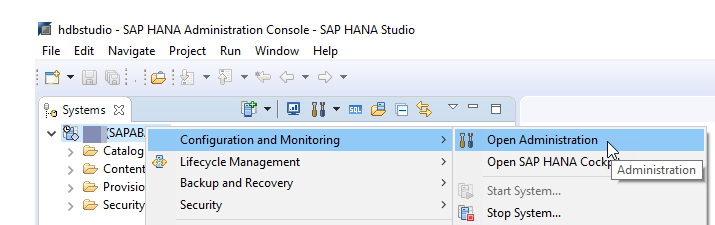
- Click the Configuration tab, and expand
webdispatcher.ini.
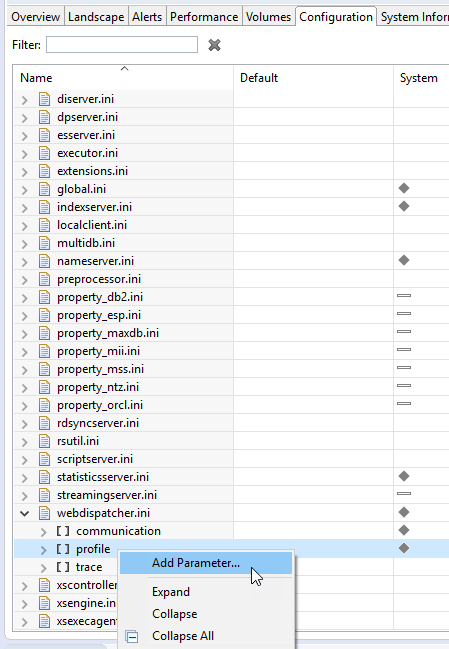
- Right-click profile, and select Add Parameter.
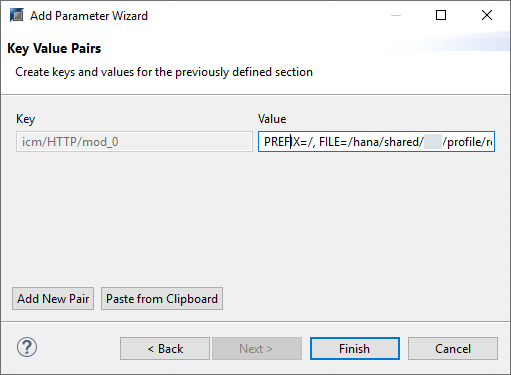
- Add a new parameter named icm/HTTP/mod_0, with the value PREFIX=/,
FILE=/hana/shared/<SID>/profile/rewrite.txt. Replace
<SID> with your three-character system ID.
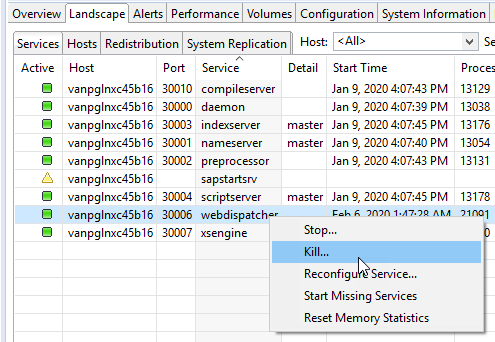
- Switch to the Landscape tab. Right-click
webdispatcher, and click Kill.
HANA's Web Dispatcher will shut down and restart automatically, which allows the
new parameter to take effect. Alternatively, you can restart the entire HANA
system.
Refer to SAP Note 2887651  for more details.
for more details.
SAP HANA on SAP Business Technology Platform (BTP) Cloud Foundry
- On your local computer, go to <HAA_ROOT> where your analytics adapter application is located.
- Open and edit mta.yaml. Under properties: add the
following COOKIES: property with the SameSite
attribute, leaving all other properties unchanged:
properties: CORS: '[{"uriPattern": "^/sap/bc/ina/(.*)$", "allowedOrigin": [{"host":"<sac-host>", "protocol":"https"}], "allowedMethods": ["GET", "POST", "OPTIONS"], "allowedHeaders": ["Origin", "Accept", "X-Requested-With", "Content-Type", "Access-Control-Request-Method", "Access-Control-Request-Headers", "Authorization", "X-Sap-Cid", "X-Csrf-Token"], "exposeHeaders": ["Accept", "Authorization", "X-Requested-With", "X-Sap-Cid", "Access-Control-Allow-Origin", "Access-Control-Allow-Credentials", "X-Csrf-Token", "Content-Type"]}]' COOKIES: '{"SameSite": "None"}' INCOMING_CONNECTION_TIMEOUT: 600000 TENANT_HOST_PATTERN: '^(.*)-<space>-haa.cfapps.(.*).hana.ondemand.com' - Save mta.yaml.
- Open and edit package.json. Change the dependency to
6.7.2:
"dependencies": { "@sap/approuter": "^6.7.2" }, - Save package.json.
- From the <HAA_ROOT> directory in a command prompt, run the following
commands to rebuild and redeploy your
application:
java -jar mta.jar --build-target=CF build cf api <api-endpoint> cf login cf deploy <HAA_ROOT>.mtar
TipFind your <api-endpoint> value (Cloud Foundry API endpoint) from your subaccount view of the BTP Cockpit.
Once deployed, verify the new version of your analytics adapter. Go to your subaccount view of the BTP Cockpit, and then check the analytics adapter User-Provided Variables. Make sure that the COOKIES variable is set to {“SameSite: “None”}.
SAP S/4HANA, SAP BW or BW/4HANA, and SAP BPC Embedded with CORS Enabled by HTTP Allowlists
If CORS was enabled through HTTP allowlists, or in other words, if CORS was configured within the UCONCOCKPIT transaction, you need to create an Internet Communication Manager (ICM) rewrite rule file to append the SameSite=None and Secure attributes to all the cookies issued by the NetWeaver ABAP application server (AS ABAP).
- Log on to the operating system of the AS ABAP system, and create a rewrite.txt file in the system profiles folder using a text editor.
- Add the following rewrite script to the file, to append the cookie attributes to compatible
web browsers, and save
it:
SetHeader sap-ua-protocol "" if %{HEADER:clientprotocol} stricmp http [OR] if %{HEADER:x-forwarded-for-proto} stricmp http [OR] if %{HEADER:forwarded} regimatch proto=http begin SetHeader sap-ua-protocol "http" end if %{HEADER:clientprotocol} stricmp https [OR] if %{HEADER:x-forwarded-for-proto} stricmp https [OR] if %{HEADER:forwarded} regimatch proto=https begin SetHeader sap-ua-protocol "https" end if %{HEADER:sap-ua-protocol} strcmp "" [AND] if %{SERVER_PROTOCOL} stricmp https begin SetHeader sap-ua-protocol "https" end if %{RESPONSE_HEADER:set-cookie} !strcmp "" [AND] if %{HEADER:sap-ua-protocol} stricmp https [AND] if %{HEADER:user-agent} regmatch "^Mozilla" [AND] if %{HEADER:user-agent} !regmatch "(Chrome|Chromium)/[1-6]?[0-9]\." [AND] if %{HEADER:user-agent} !regmatch "(UCBrowser)/([0-9]|10|11|12)\." [AND] if %{HEADER:user-agent} !regmatch "\(iP.+; CPU .*OS 12_.*\) AppleWebKit\/" [AND] if %{HEADER:user-agent} !regmatch "\(Macintosh;.*Mac OS X 10_14.*(Version\/.* Safari.*|AppleWebKit\/[0-9\.]+.*\(KHTML, like Gecko\))$" begin RegIRewriteResponseHeader set-cookie "^([^=]+)(=.*)" "$1$2; SameSite=None; Secure" RegIRewriteResponseHeader set-cookie "^([^=]+)(=.*; *SameSite=[a-zA-Z]+.*); SameSite=None; Secure" $1$2 RegIRewriteResponseHeader set-cookie "^([^=]+)(=.*; *Secure.*); Secure" $1$2 end - Log on to the AS ABAP system from SAP GUI with a system administrator user account.
- Go to transaction RZ10, and edit the AS ABAP system's DEFAULT profile.
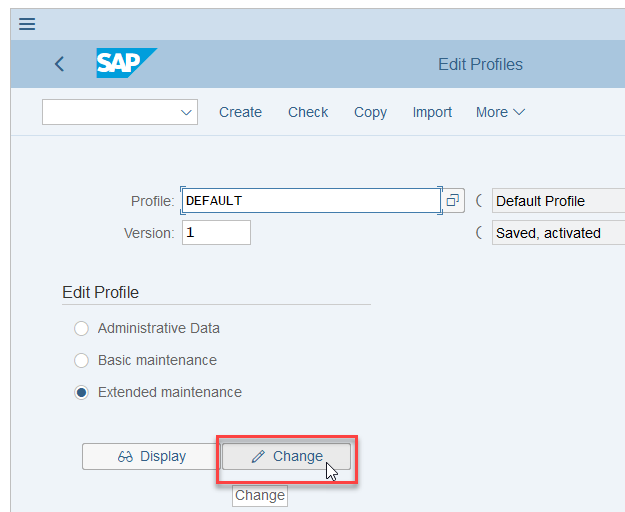
- To enable HTTP rewriting and point to the rewrite file, click
Parameters, and add the following profile
parameter:
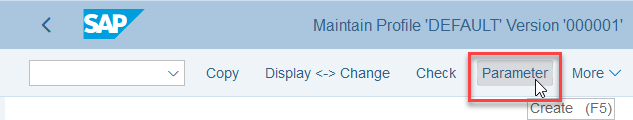
icm/HTTP/mod_0 = PREFIX=/,FILE=$(DIR_PROFILE)/rewrite.txt
In this example, the rewrite file is rewrite.txt, in the system profiles folder.
- Save the change.
- Restart the AS ABAP system.
Refer to SAP Note 2887651  for more details.
for more details.
SAP S/4HANA, SAP BW or BW/4HANA, and SAP BPC Embedded with CORS Enabled by ICM Rewrite Script
If CORS was enabled with an Internet Communication Manager (ICM) rewrite script, the NetWeaver ABAP application server (AS ABAP) already has an existing ICM rewrite file. To append the SameSite=None and Secure cookie attributes to the cookies, follow these steps:
- Find the path to the ICM rewrite file by inspecting the profile parameter icm/HTTP/mod_0 in the system's DEFAULT profile.
- Log on to the operating system with the <SID>adm user.
- Edit the ICM rewrite file. At the end of the file, append the following
script:
SetHeader sap-ua-protocol "" if %{HEADER:clientprotocol} stricmp http [OR] if %{HEADER:x-forwarded-for-proto} stricmp http [OR] if %{HEADER:forwarded} regimatch proto=http begin SetHeader sap-ua-protocol "http" end if %{HEADER:clientprotocol} stricmp https [OR] if %{HEADER:x-forwarded-for-proto} stricmp https [OR] if %{HEADER:forwarded} regimatch proto=https begin SetHeader sap-ua-protocol "https" end if %{HEADER:sap-ua-protocol} strcmp "" [AND] if %{SERVER_PROTOCOL} stricmp https begin SetHeader sap-ua-protocol "https" end if %{RESPONSE_HEADER:set-cookie} !strcmp "" [AND] if %{HEADER:sap-ua-protocol} stricmp https [AND] if %{HEADER:user-agent} regmatch "^Mozilla" [AND] if %{HEADER:user-agent} !regmatch "(Chrome|Chromium)/[1-6]?[0-9]\." [AND] if %{HEADER:user-agent} !regmatch "(UCBrowser)/([0-9]|10|11|12)\." [AND] if %{HEADER:user-agent} !regmatch "\(iP.+; CPU .*OS 12_.*\) AppleWebKit\/" [AND] if %{HEADER:user-agent} !regmatch "\(Macintosh;.*Mac OS X 10_14.*(Version\/.* Safari.*|AppleWebKit\/[0-9\.]+.*\(KHTML, like Gecko\))$" begin RegIRewriteResponseHeader set-cookie "^([^=]+)(=.*)" "$1$2; SameSite=None; Secure" RegIRewriteResponseHeader set-cookie "^([^=]+)(=.*; *SameSite=[a-zA-Z]+.*); SameSite=None; Secure" $1$2 RegIRewriteResponseHeader set-cookie "^([^=]+)(=.*; *Secure.*); Secure" $1$2 end - Restart the AS ABAP system.
Refer to SAP Note 2887651  for more details.
for more details.
SAP BusinessObjects BI Universe
The SAP BusinessObjects Live Data Connect component, together with the Tomcat server that it runs on, already issues cookies with the Secure attribute. Therefore, we just need to configure the Live Data Connect component to issue cookies with the SameSite attribute set to None.
- Check the version of the Tomcat server where the Live Data Connect component
runs. If the Tomcat version is lower than 8.5.50 or 9.0.30, upgrade or migrate
it to at least 8.5.50 or 9.0.30, respectively.
See the migration guides at http://tomcat.apache.org/migration.html
 .
. - If you upgraded or migrated your Tomcat server, make sure to migrate the Live Data Connect
component as well. This can be done by copying the
sap#boc#ina.war file and the
sap#boc#ina directory under
<original_tomcat_root>/webapps to the new Tomcat
server. Make sure all the Live Data Connect settings are preserved, and HTTPS is
properly configured.
For more details, refer to Configuring SAP BusinessObjects Live Data Connect and Setting up SAML authentication in the SAP BusinessObjects Live Data Connect Installation and Security Guide.
- Go to the <Tomcat_root>/webapps/sap#boc#ina/METADATA-INF directory.
- Open the xml file in a text editor, and insert the CookieProcessor segment
to set the SameSite attribute to None. It
should look like
this:
<Context docBase="" path="/sap/boc/ina" reloadable="false" useHttpOnly="true"> <CookieProcessor className="org.apache.tomcat.util.http.LegacyCookieProcessor" sameSiteCookies="none" /> </Context>Save the file.
- Restart the Tomcat server.
Refer to SAP Note 2889975  for more details.
for more details.